Risk‑Focused Cybersecurity, Open‑Source Roots
000 +
Offensive security engagements delivered across industries, from red teaming to adversary emulation
00 +
Open‑source projects actively maintained
00000 +
Practitioners trained through hands‑on courses and workshops
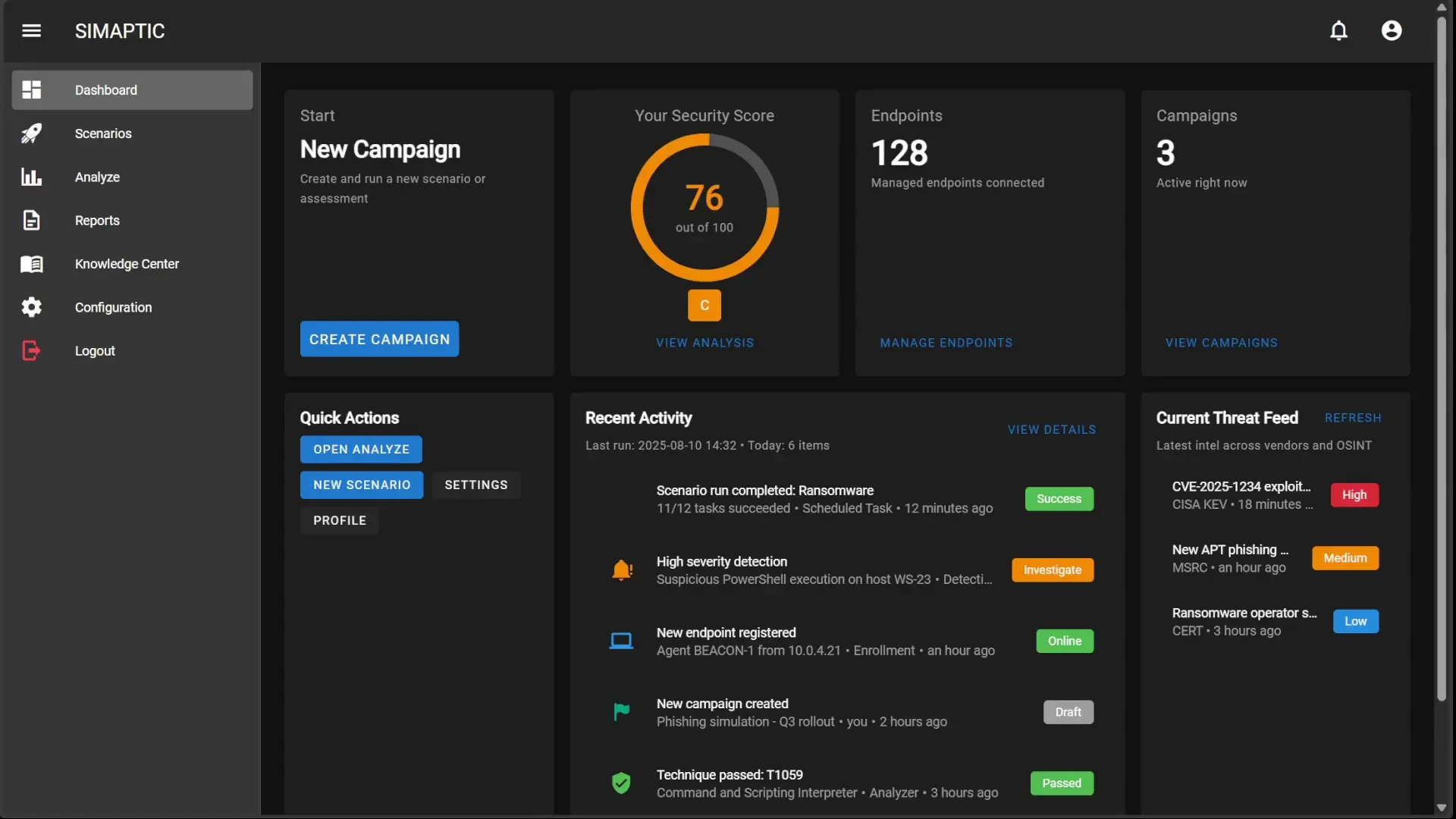
What News Do We Have Today?
Empire 6.0 – New Agents, Plugin Marketplace, and Major Updates
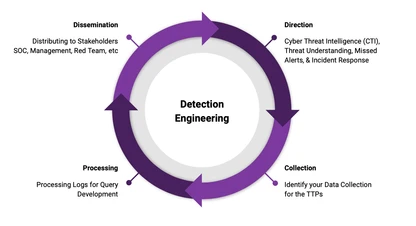
Read More about empire 6.0 – new agents, plugin marketplace, and major updatesIronPython Tradecraft: Offensive Techniques Using the DLR
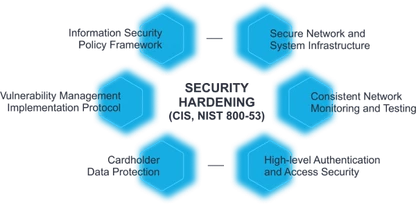
Read More about ironpython tradecraft: offensive techniques using the dlrSecurity Services That Reduce Risk
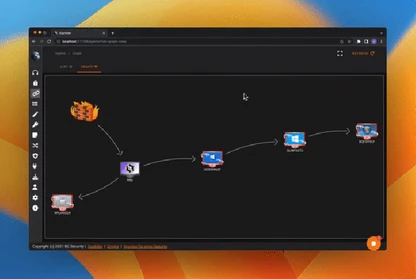
A Realistic, Risk‑Focused Engagement Process
Scope & Threat Modeling
We align on objectives, rules of engagement, and success criteria. Then we model likely adversaries for your organization and identify the TTPs that matter most.

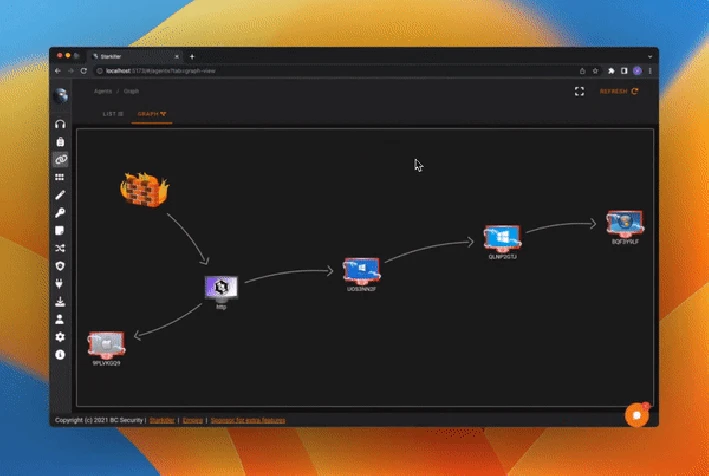
Emulation Plan Mapped to MITRE ATT&CK
We design a tailored emulation plan that maps tactics, techniques, and procedures to your controls and constraints. Over‑tooling is avoided in favor of realistic tradecraft.

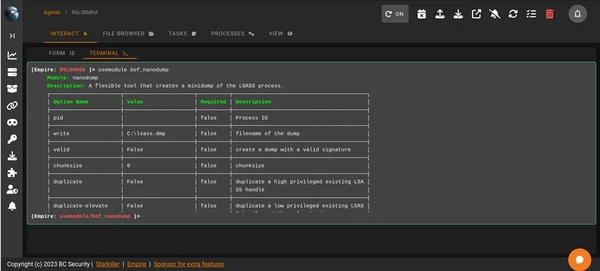
Execute, Measure, and Collaborate with Defenders
We run the operation, provide actionable findings with clear risk context, and share feedback with blue teams, sometimes intentionally getting caught to improve detection and response.

Ready to Emulate Real Threats and Improve Defense?
Work with BC Security to plan a focused penetration test, red team engagement, or team training. We’ll map TTPs to your environment and help you make informed, risk‑based decisions.
Satisfaction Rate
Our clients consistently report high levels of satisfaction
Successful Projects
our team of consultants brings a wealth of expertise.
Years of Experience
Our strategies have generated over $50 million.