Applying Systems Engineering to Cyber Risk: Functional Decomposition and the Lemonade Stand
Bridging Policy and Implementation in Cyber Risk Management
Recently, while discussing cyber risk management with a customer, they made the observation that there is a lot of training for top-level risk management—like CISSP—that focuses on building policy. There’s also a lot of training on technical details, but not much information on how to transition between those plans and the technical details.
Let’s say your network admin has suddenly been tasked with implementing security at your company. Where do you start? How do you determine where to spend money first and what tasks should be prioritized? To help remedy that, this will be the first entry in a series of articles on applying systems engineering to evaluate a business and start building those implementation plans.
Lessons from the Air Force
When I worked at the Air Force Operational Test Evaluation Center, we were tasked with evaluating the effectiveness of weapon systems—specifically, fighter aircraft. One aspect of this was identifying vulnerabilities in the weapon system. This wasn’t necessarily about cyber vulnerabilities but any weakness that could impact combat performance.
For example, if the fighter couldn’t detect a target approaching from the left side, that would be a significant combat vulnerability—but not a cyber one. We conducted live tests, but before that, we used a process called functional decomposition to help design our tests.

What Is Functional Decomposition?
Functional decomposition is a systems engineering process where a complex system is broken down into smaller, more manageable functions. This allows for focused evaluation of individual functions and processes.
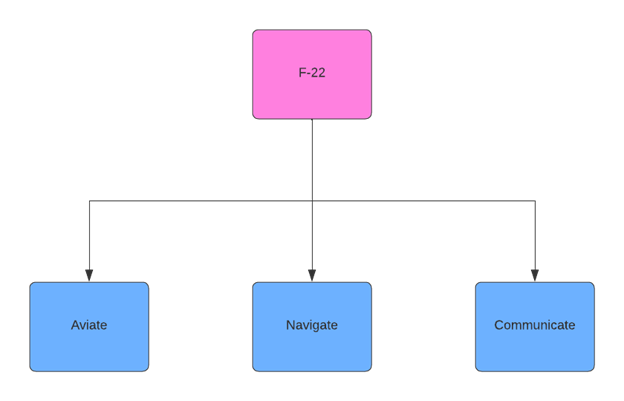
If that sounds abstract, let’s look at an example. I’m partial to the F-22, since I ran the first cyber assessment against it. Traditionally, when doing a functional decomposition of an aircraft, there are three core functions that make it an aircraft:
- The ability to aviate
- The ability to navigate
- The ability to communicate
In other words, it must be able to fly, know where it is, and communicate with other aircraft and air traffic controllers.
Applying Functional Decomposition to Business
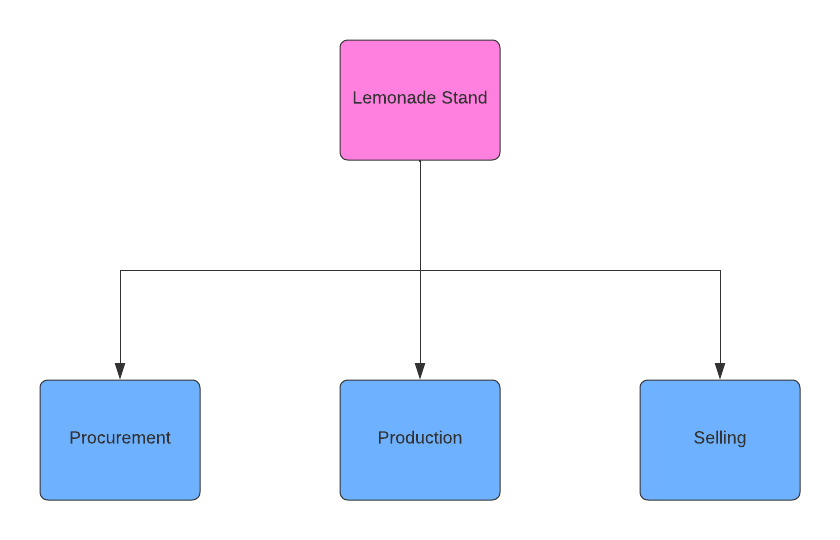
A business can also be represented as a system. It has a core mission that it’s attempting to achieve and thus has critical functions that it must complete. Let’s move on from the airplane and refocus on a simple business: a lemonade stand on a street corner.
This lemonade stand makes lemonade by hand and sells it to people walking to the park. To start the functional decomposition process, we’ll identify its core activities. While there’s some subjectivity, we’ll define three main functions:
- Procurement
- Production
- Selling
These represent getting supplies, making the lemonade, and selling it.
Breaking Down the Functions
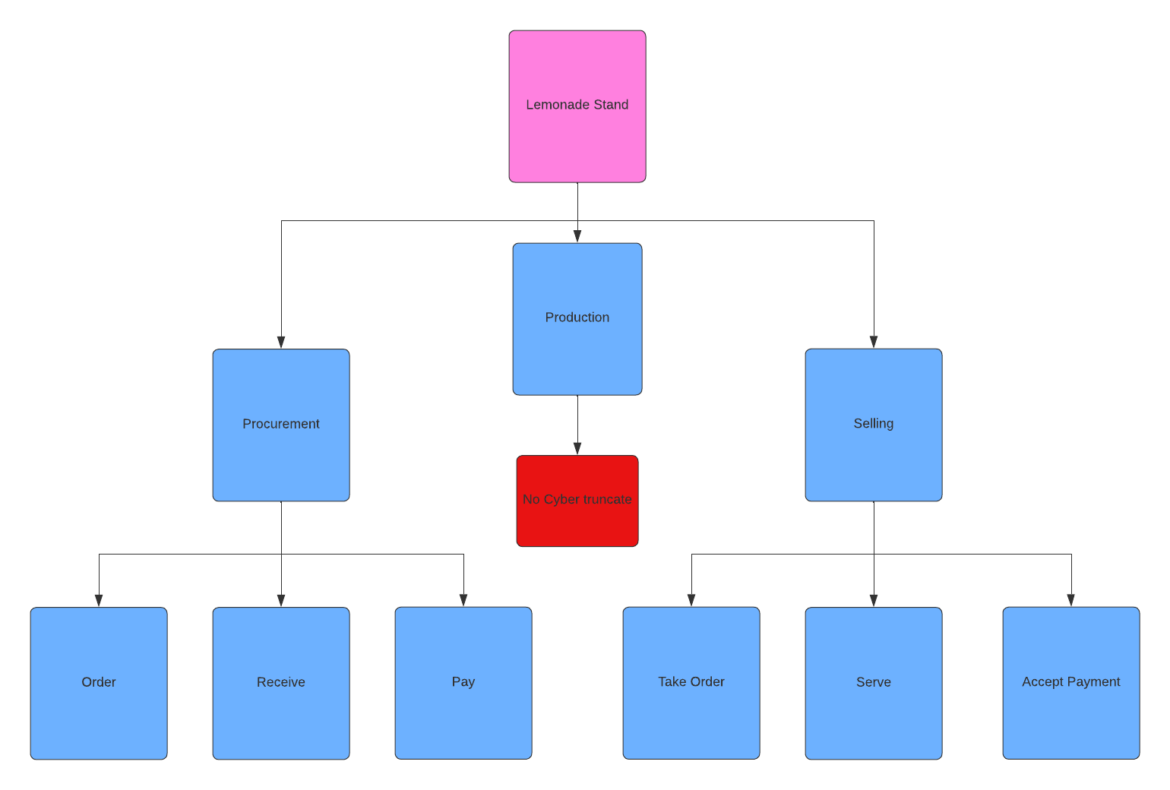
Procurement
This includes getting lemons, sugar, cups, and materials for signs. Since the lemonade stand has all supplies delivered, we can break Procurement into:
- Order
- Receive
- Pay
Production
All production is manual—no electronics are used, and lemonade is made fresh daily. We can break this process into:
- Prep
- Mix
- Clean
Here, we can apply our cyber lens. Since no digital systems are used in production, there’s minimal cyber exposure, so this branch can be truncated here.
This demonstrates how decomposition helps identify a company’s threat surface and where resources should be focused.
Selling
Finally, Selling includes taking the customer’s order, serving the product, and accepting payment. These are our three functions:
- Order
- Serve
- Accept Payment
Connecting to Cyber Risk: MRAP-C
In a real analysis, we’d continue decomposing each tier until identifying the core underlying steps for each function. This is the foundation of a Mission Analysis, the first step in the Mission-Based Risk Assessment Process for Cyber (MRAP-C)—a framework published by the DoD that Anthony helped shape.
At BC Security, we use a modified version of MRAP-C, which can be broken down into these phases:
1. Business Analysis
Identify Business Objectives and Critical Processes Determine the critical functions and operations required to achieve business goals.
Develop Operations Threads Analyze business operations to understand the sequence of events and processes critical to mission success.
2. Threat Assessment
Identify Threats Identify potential cyber threats that could impact business operations at critical points identified in the business analysis.
Threat Analysis Assess the capabilities, intentions, and potential impacts of identified threats on business objectives. Identify the sophistication of the probable threat actor.
3. Vulnerability Assessment
Tabletop Analysis Using identified threats, review business operations to find failure points and map functions to hardware assets.
Evaluate Vulnerabilities Conduct vulnerability scans, penetration tests, and asset cataloging to validate assumptions. Compare real-world implementations vs. documented expectations.
4. Risk Assessment
Risk Analysis Based on validated findings from the Vulnerability Assessment, produce risk reporting for the organization.
Risk Prioritization Prioritize risks based on their potential impact and likelihood of occurrence.
5. Remediation and Residual Risk Identification
Remediation Invest funds and implement changes to address prioritized risks. This step may take months or years.
Residual Risk Identification Once risks are remediated, reanalyze the business to identify remaining risks.
So far, we’ve conducted the Identify Business Objectives and Critical Processes step for our lemonade stand. We’ve identified the core functions to analyze in our Operations Threads.
The operation threads serve two functions:
- They provide attack vignettes to build real-world application and sequencing for functions.
- They allow us to start mapping functions to components—and as we’ll explore in the next installment, multiple functions are often handled by a single system, increasing both importance and likelihood of attack.
Ready to Transform Your Business?
Partner with our team of experts to unlock your business’s full potential. Schedule your free consultation and discover how we can help you.
