Offensive Security and Red Teaming Training
Offensive Tooling Consulting & Support
Expert guidance for deploying, operating, and extending open-source offensive security tooling in safe, controlled ways.
Contact Us
Adversary Emulation & Red Team Operations
Emulate real-world threat actors to measure and improve your organization’s detection, response, and resilience.
Contact Us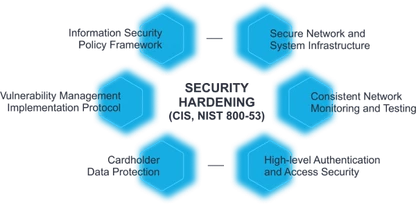
Security Assessments & Hardening
Targeted assessments and hardening engagements across Windows, Active Directory, and cloud identity to reduce attack paths.
Contact Us
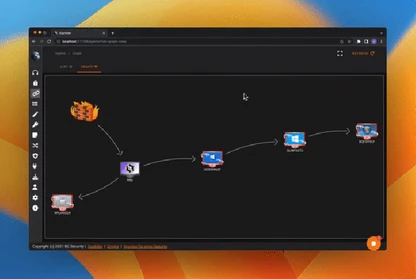
Malware Emulation & Ransomware Readiness
Safely emulate malware behaviors and ransomware kill chains to test prevention, detection, and response without business impact.
Contact Us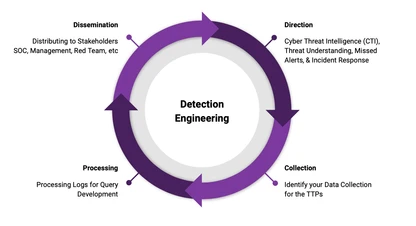
Purple Teaming & Detection Engineering
Collaborative exercises that pair operators with defenders to tune detections, close gaps, and strengthen response.
Contact Us
Security Training
Hands-on operator training to emulate real threat actors and tradecraft.
Contact UsReady to Transform Your Business?
Partner with our team of experts to unlock your business’s full potential. Schedule your free consultation and discover how we can help you.
Satisfaction Rate
Our clients consistently report high levels of satisfaction
Successful Projects
our team of consultants brings a wealth of expertise.
Years of Experience
Our strategies have generated over $50 million.